Over the Independence Day holiday weekend, High Wire Networks’ Overwatch Security Operations Center (SOC) stopped a cyberattack within minutes of detection.
On July 3rd at approximately 3 p.m., Overwatch security analysts received an alert of a cyberattack on the network of a civil engineering firm. The SOC immediately triggered a kill/quarantine action through the Security Orchestration and Automation Response (SOAR) tool, with guidance and expertise of a Tier 3 security analyst for the remediation process.
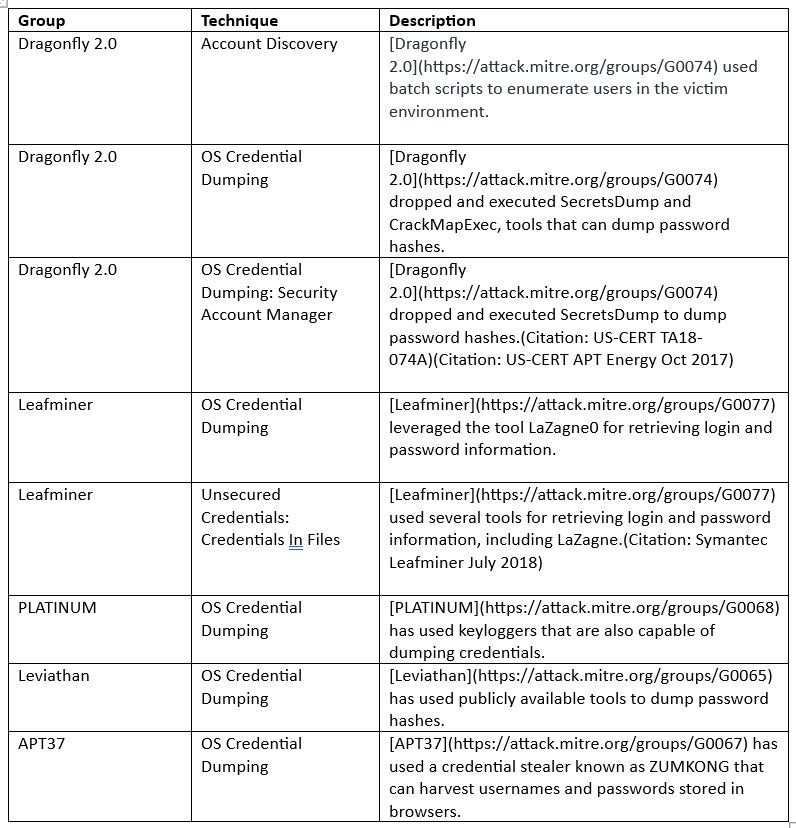
This customer only had Managed Endpoint Detection and Response (EDR), so there were some gaps in what the analysts could see. They knew that an unknown single IP address was trying to talk to multiple hosts. As the mitigation process was underway, bad actors initiated a second attack, but Overwatch had already shut down the customer’s domain controller. The attackers used a paid-for program called XenArmour in order to attempt to dump credentials.
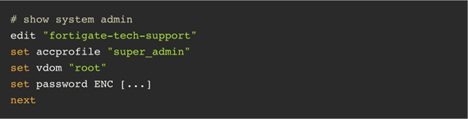
After learning that the unknown IP was a Fortinet firewall, it was confirmed that FortiGate was running on vulnerable version 4.2.2. FortiGate was immediately patched, unknown accounts were deleted, and the team continued to monitor the situation.
The next day, Overwatch detected another lateral movement attempt and immediately responded to the incident. After further inspection of FortiGate, the security analysts realized that an unknown administration account had not been deleted the night before, and persistence was set up through an SSH rule. Overwatch also noticed an indicator pointed out by Fortinet was in the System Logs user=”Local_Process_Access,” which confirmed that the firewall was breached due to the CVE-2023-27997 exploit.
Overwatch and the managed services provider (MSP) partner collaborated to reset all passwords, disable unused accounts, remove old software, and roll back any changes the attacker had made on FortiGate. The incident was resolved within 30 minutes of the initial attack phase. The MSP partner was proud of Overwatch’s quick response time, ability to manage and respond to threats, and guidance in getting his end customer’s system back up and running. Aaron Martin, Overwatch Director of Security Engineering, worked throughout the weekend and into the holiday to ensure the partner could fully restore his customer’s system.
Overwatch also set up an Extended Detection and Response (XDR) integration to EDR as another layer of protection and reviewed the customer’s environment to ensure that data was not exfiltrated.
This attack could have become catastrophic had the MSP not deployed Overwatch Managed Cybersecurity services for the customer, which includes the monitoring and response from Overwatch 24/7 SOC and SOAR technology. The end customer expressed had this not been in place, they could have easily been a victim of ransomware and data exfiltration.
Indicators of Compromise (IOC)
Known File Hashes Present in findings:
File Hash SHA1: 651cd610174f53fe74f34d036e45da2dad75e1f1
No known files associated with the hash above.
File Hash SHA256: eda18761f3f6822c13cd7beae5af2ed77a9b4f1dc7a71df6ab715e7949b8c78b
XenArmor All-In-One Password Recovery Pro Command-line a paid for tool known for dumping passwords.
Fortinet System Logs:
user=”Local_Process_Access”
Admin1 account created
VPNAdmin account created
Support22 VPN account created
SSH rule open to the internet
Malicious IP addresses found during the investigation for the FortiGate:
185.220.101.59 – Known Malicious address out of Germany likely a TOR exit node.
80.66.83.115 – Known Malicious address ASN XHOST INTERNET SOLUTIONS LP which appears to be a Russian based reseller of OVH servers
165.231.182.19 – Known malicious VPN (Private Internet Access) Out of Estonia, appears to be a possible C2(command and control server)
109.70.100.71 – Known Tor exit node out of Austria
MSP Partner Testimonial
“Had Overwatch not been in place, I definitely wouldn’t have been able to detect the attack as early as we did and we could have had a much bigger problem,” our partner said. “There are a lot of good security programs out there, but Overwatch is one of the best.”
If you’re interested in partnering with Overwatch and providing your end customers with expertise, dedication, and active remediation in the event of a cyberattack, contact overwatchsales@highwirenetworks.com for more information.
Tactics and Techniques
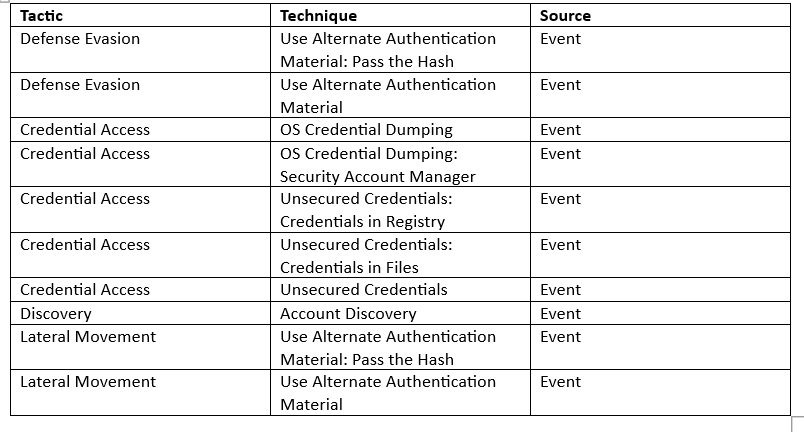
Adversarial Groups
See a detailed description of the adversarial groups that may be related to this incident.