Overwatch MXDR delivers powerful open extended detection and response (Open XDR) for end-to-end cybersecurity solutions.
Cybercrime is rampant and businesses are demanding more from their security providers. Cloud adoption and work from home or anywhere – on any device – are blurring infrastructure boundaries as never before, creating an ever-expanding surface for cyberattacks. Overwatch MXDR condenses the entire surface into an intelligent, manageable stream for more robust security, better threat identification and faster responses.
What is MXDR?
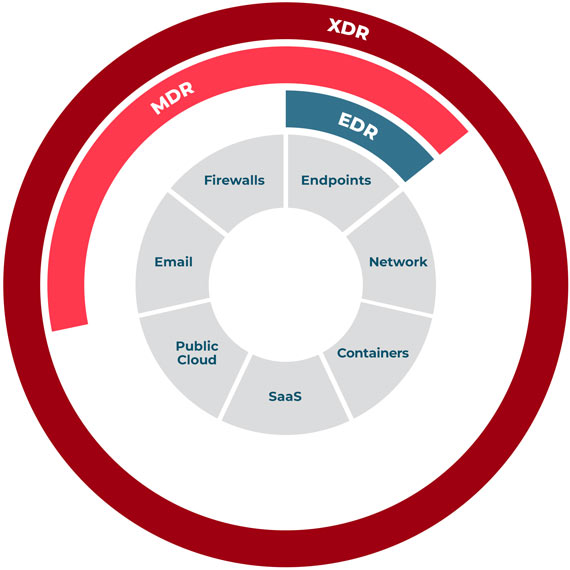
Managed Extended Detection and Response (MXDR) is a vendor-agnostic XDR solution that consolidates multiple security products into a single platform to better detect and respond to threats. This centralized platform empowers security teams to more quickly and easily identify threats and breaches and provides context around incidents that can bolster and speed up response and remediation.
Managed XDR Infrastructure
The ability to achieve robust XDR through integration with existing infrastructure
“Limitless” potential to adopt and integrate new technologies (as opposed to single-vendor solution limits)
Future-proof ability to adopt new and cutting-edge infrastructure and security solutions
What is MXDR?
Managed Extended Detection and Response (MXDR) is a vendor-agnostic XDR solution that consolidates multiple security products into a single platform to better detect and respond to threats. This centralized platform empowers security teams to more quickly and easily identify threats and breaches and provides context around incidents that can bolster and speed up response and remediation.
Managed XDR Infrastructure
The ability to achieve robust XDR through integration with existing infrastructure
“Limitless” potential to adopt and integrate new technologies (as opposed to single-vendor solution limits)
Future-proof ability to adopt new and cutting-edge infrastructure and security solutions
Overwatch MXDR
Overwatch MXDR from High Wire Networks is a turnkey solution built from best-in-class technologies and a best-practices security framework from the Overwatch Cybersecurity team. It’s an integral part of our managed cybersecurity services suite, delivering AI-powered MXDR solutions from the market-leading team and tools in the Overwatch 24/7 Security Operations Center (SOC).
Built-in integration with other Overwatch solutions
Integration with other systems, for GRC and more
APIs for data export
Built-in event-response and case-management capabilities:
- Create a trouble ticket
- Trigger email, Slack and restful API alerts
- Automatically send out PDF reports
- Signal firewalls to take appropriate action
Comprehensive, automatic sensor-based data collection
Physical (on-premises) and cloud visibility
Integrated IDS/IPS paired with AI to reduce false positives
50,000+ detections for known and unknown behaviors, mapped to the cybersecurity kill chain
Simple, easy-to-use GUI dashboards
Advanced analytics and data-lake mining
Built-in integration with other Overwatch solutions
Integration with other systems, for GRC and more
APIs for data export
Built-in event-response and case-management capabilities:
- Create a trouble ticket
- Trigger email, Slack and restful API alerts
- Automatically send out PDF reports
- Signal firewalls to take appropriate action
Benefits of Overwatch MXDR
Overwatch MXDR arms High Wire cybersecurity partners with a market-leading solution that delivers operational and security benefits to MSPs, MSSPs and their customers. Like all Overwatch cybersecurity solutions, managed XDR from Overwatch is backed by experienced channel and cybersecurity teams.
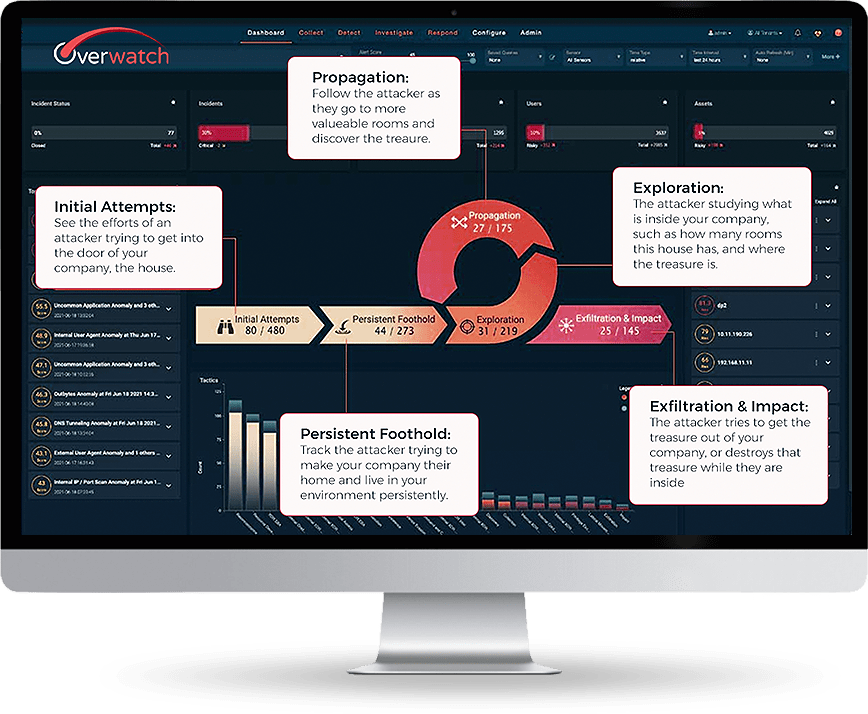
Track Threats in Real-Time with Overwatch MXDR
Overwatch MXDR’s end-to-end visibility lets you see in real-time how a threat is manifesting step-by-step in your infrastructure.
This graphical representation of an actual attack shows all the network points touched and all the logical and physical associations within the attack. Analysts can use alerts to visually compare telemetry data with graphical analysis for an enriched view of the event. Most importantly, these views are generated automatically (without taking up analyst time) on an incident-by-incident basis, facilitating rapid and effective response.
Security Benefits
- Protects your entire attack surface
- Enhances existing infrastructure with superpowered AI
- Delivers best-in-class intelligence regardless of existing security products and services
- Deploys across network, cloud and endpoint infrastructure
- Generates exponential improvements in detection (MTTD) and response (MTTR) times
- Developed and delivered by High Wire’s market-leading SOC team
Cost Benefits
- Leverages existing infrastructure
- Fewer incidents to manage and recover from
- Faster recovery time
- Expandable and extensible in vendor-agnostic fashion
- Streamlined sourcing and ops
Overwatch MXDR Resources
Latest News and Events from Overwatch
Latest News & Events from Overwatch
Overwatch
Overwatch Expands Cybersecurity Innovation with AI- Driven Hyper-Automation, Delivering Unfair Advantage to MSPs BATAVIA, Ill., March 18, 2025 — High Wire Networks, Inc. (OTCQB: HWNI) is redefining cybersecurity for Managed Service Providers (MSPs) and their customers… Read more
News & Events
Overwatch
High Wire’s Overwatch Expands Portfolio to Include Critically Needed Professional Services Notches First Win with Cyber Advisory Consulting Engagement FOR IMMEDIATE RELEASE BATAVIA, Ill., February 25, 2025 — High Wire Networks, Inc. (OTCQB:… Read more
News & Events
Overwatch
High Wire Networks Announces Appointment of Kim L. Jones as CISO for Overwatch [Batavia, IL]—January 3, 2025 — High Wire Networks is proud to announce the addition of Kim L. Jones to Overwatch,… Read more